Security for containers, Kubernetes, and Cloud. This is the catchphrase presented prominently on the Sysdig website, a tool that supports the implementation of DevSecOps. This article provides an overview of the Sysdig product and its place in modern software development. We’ve written an introduction to Sysdig before.
DevSecOps
The term DevSecOps is short for Development, Security and Operations. It is an evolution of DevOps and implements security practices into the methodology. This implementation starts a number of years ago when it became clear that security plays a crucial role in modern software development, but that this role is quite different from the way security works in a traditional environment. Nowadays, dev and ops need to be security-aware in everything they do, it is necessary to embed security in every step of a CI/CD pipeline, and automate as much as possible in order to prevent delivery- and deployment lag. This a paradigm shift that results in new tools and a new way of working.
A bird’s eye view of Sysdig
An example of such a tool is Sysdig. It aims to secure the DevOps workflow and delivers monitoring, security and forensics for container workloads and microservices. It is possible to deploy Sysdig in various environments across the usual Public Clouds, OpenShift and Tanzu.
Open Source roots
Dating back to 2014, Sysdig started out as a Linux command-line tool for system monitoring. New features appear regularly, for example, an enhancement to support container monitoring. It is still available and under active development.
The commercial offering is Sysdig Secure DevOps platform, built on several open-source products. Falco, a Cloud runtime security engine developed by Sysdig itself dates back to 2016. The next is Anchor Engine, which provides container vulnerability analysis. Cloud Custodian is used as a rules engine that allows fine-grained control (such as configuration checks) on Public Cloud providers. Finally, Prometheus is used for monitoring.
Sysdig platform functionality
The Sysdig platform allows for control over build, run and respond processes in modern software development and operations. Within build, it is possible to monitor and act upon vulnerabilities in CI/CD pipelines such as Bamboo or Jenkins, or do runtime CVE monitoring on images in registries such as Harbor and Quay. In run, application data (in the form of metrics, events and security policies) are harvested from containers or even directly from Java application code and its runtime, by means of JRE and JVM monitoring using the JMX protocol. Respond, finally, allows sending out alerts to platforms such PagerDuty, but integration with SIEM platforms is a possibility as well.
Agent-based approach
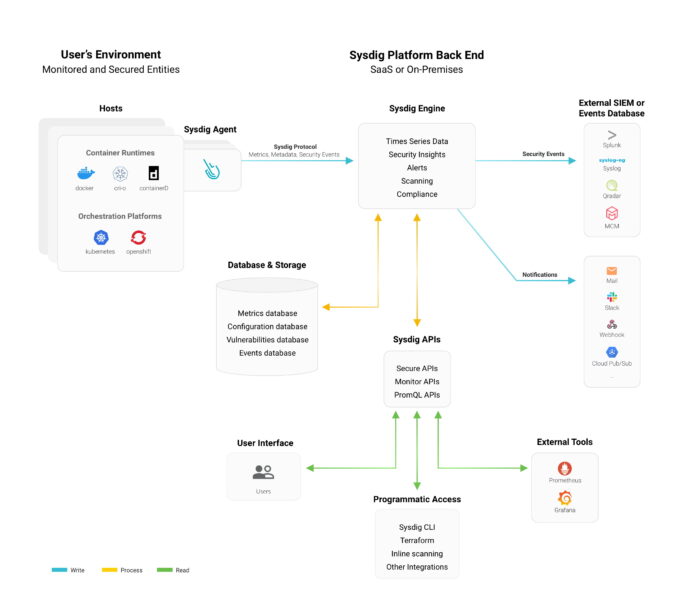
Sysdig uses an agent-based approach, which means it installs as an agent on a host (it can be a container itself within either a Kubernetes or OpenShift node, a VM, bare metal or Cloud vendor) collects monitoring and security information from a variety of sources, such as Prometheus endpoints, containers and their runtimes, orchestration API’s from an underlying container platform, but also host information. Sysdig uses a plugin architecture that enables it to monitor specific applications as well. A list of supported applications is available.
Sysdig backend
The Sysdig agent communicates with a backend, which can either be a SaaS or deployed on-premises. The backend processes the host messages and stores the data in an internal metric store, in the form of time series and event data, enriched with metadata containing for example the actual and current state of a Kubernetes cluster. It is possible to share events with other platforms, such as Syslog, PagerDuty or Slack.
Data access
Access to the data stored in Sysdig is possible through APIs. Three of these exist: the monitoring API, security API and PromQL API for querying the data and presenting output to PromQL compatible solutions such as Grafana.
Sysdig architecture
Alternatives
A look at the Cloud Native Landscape shows 47 companies active in the Cloud security field, with a market cap of $1.66T. That is not as large as the Cloud database or CI/CD field (which have market caps of $5-6T), but it is still a significant capitalization – larger than the API gateway category, for example. The alternatives fall apart into two categories, basically: monitoring and security tools that were available pre-Cloud (such as Nagios and its derivatives) and those that are post-Cloud (such as Aquasec or Data Dog).
Pre and post Cloud platforms
The difference with the pre-Cloud tools is mainly that Sysdig focuses specifically on container monitoring security, whereas the other platforms offer a broader perspective and monitor servers, wider infrastructure and databases as well. In the post-Cloud platforms, the market seems to consolidate at a rapid rate, with for example Twistlock acquired by Palo Alto Networks and Stackrox by Red Hat. This means Sysdig will have to compete against larger companies. The market, however, is big enough and these acquisitions only underline the importance of Cloud security and monitoring.
Choosing Sysdig
From a comparison perspective, which platform to choose depends on a lot of factors, such as how broad you are willing to define your monitoring and security horizon. If you are a Java shop with the intention to monitor the entire flow of your application from build to run and want to have integrated, real-time security scanning, Sysdig is a great choice. From the perspective of data presentation in dashboards, a platform such as Data Dog might have the edge. Sysdig integrates with Grafana for dashboarding, but it does not offer the fine-grained presentation controls that Data Dog has.
Pricing
Sysdig is quite transparent about its pricing model. There is a free tier that runs in one AWS region, runs once a day and scans a maximum of 250 images per month. Next to that one, a monitoring tier and a security tier exist which you pay for per host. The pricing page contains a handy calculator, which lets you easily find out how much you will pay for a given number of cloud accounts and hosts.
Additional information
As an interesting extra, Sysdig publishes a yearly report on container security and usage. It uses anonymized data harvested from Sysdig customers and presents key trends in the security for containers, Kubernetes, and cloud space.